TrustZone for Cortex-M processors is on the way! There has already been an announcement from Nuvoton that they will be releasing the worlds first Cortex-M23 processor, the Cortex-M2351, that will include support for Arm TrustZone. The problem for many IoT developers though is that they are ready to start learning TrustZone now but don’t have access to any silicon or development kits that they can use to start honing their skills. In this post, I’m going to point to developers to useful resources to get up to speed on TrustZone and also show them how they can start to look at example projects that will help them get up to speed quickly.
The simplest way to get started with developing a Cortex-M TrustZone application at the moment is to do so through a fixed virtual processor (FVP). The Keil MDK5 for Arm includes a FVP simulator along with the several different code examples that can be used to explore TrustZone applications. The first step is to download Keil MDK from the keil.com website and install it on a development machine.
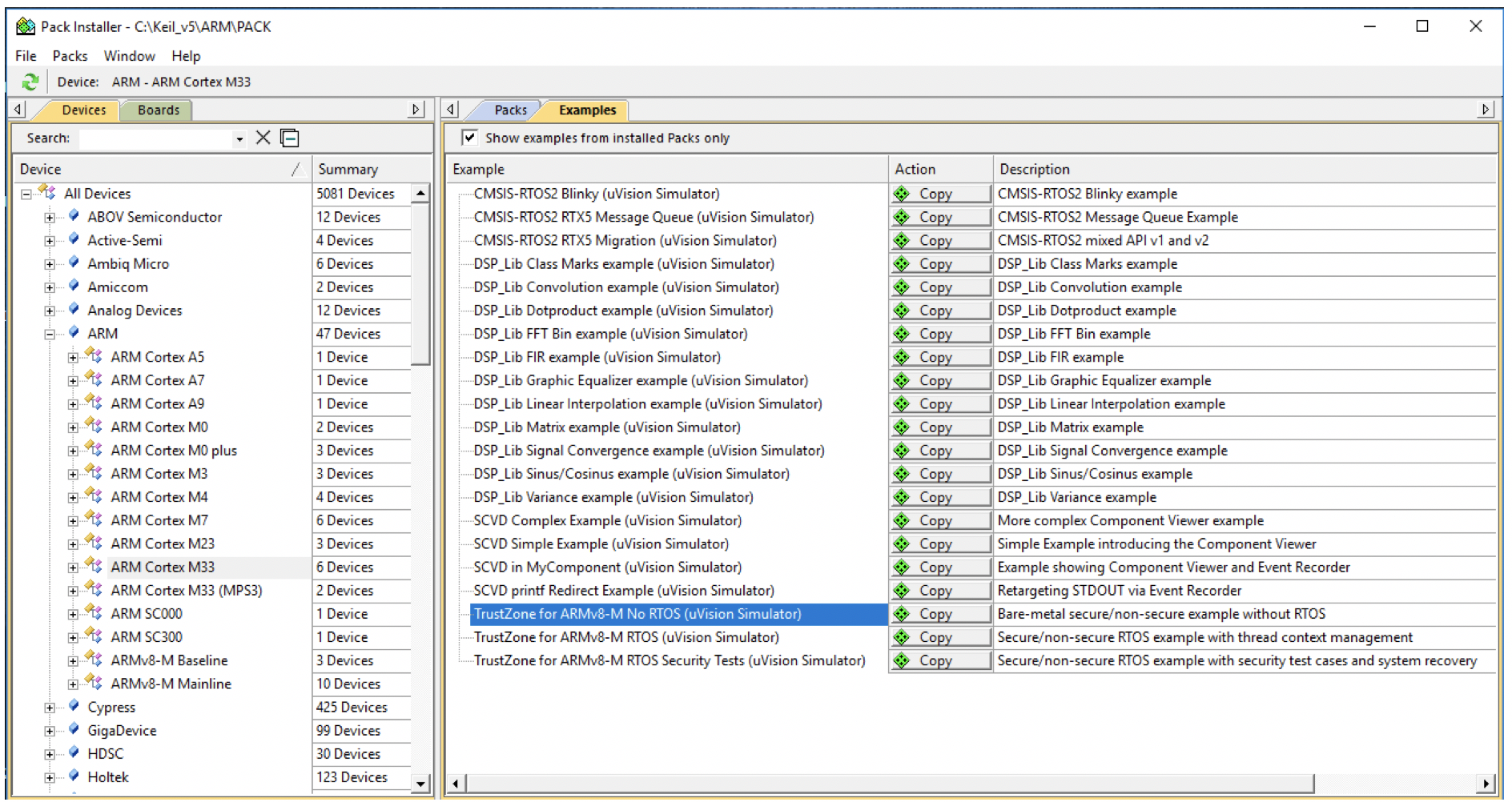
Next open the Keil pack installer and under the Devices tab, locate ARM -> All Devices -> ARM, select ARM Cortex M33. Under the Examples tab, there will be several different example projects that can be simulated but the last three are TrustZone examples! This can be seen in the image below:
These three examples provide a developer with an increasing complex example on how to use TrustZone. In the first example, the TrustZone for ARMv8-M No RTOS, developers are provided with a bare-metal implementation without an RTOS. Developers can start to understand how to configure the secure and non-secure memory, interrupts and peripherals and how to jump between the secure and non-secure world. This example should be examined first along with reading the Keil application note 291 on Using TrustZone on ARMV8-M. Walking through these together will provide the TrustZone foundations that every developer needs to get started. Once the foundation has been laid, developers can then examine the more complex examples on how to use a RTOS and perform security checks on an application.
When a developer has successfully examined the examples, they can start to experiment by modifying the existing examples or trying to build a project from scratch. One of the first things a developer will notice is that TrustZone applications are broken up into two separate applications, the secure and non-secure application as shown in the image below:
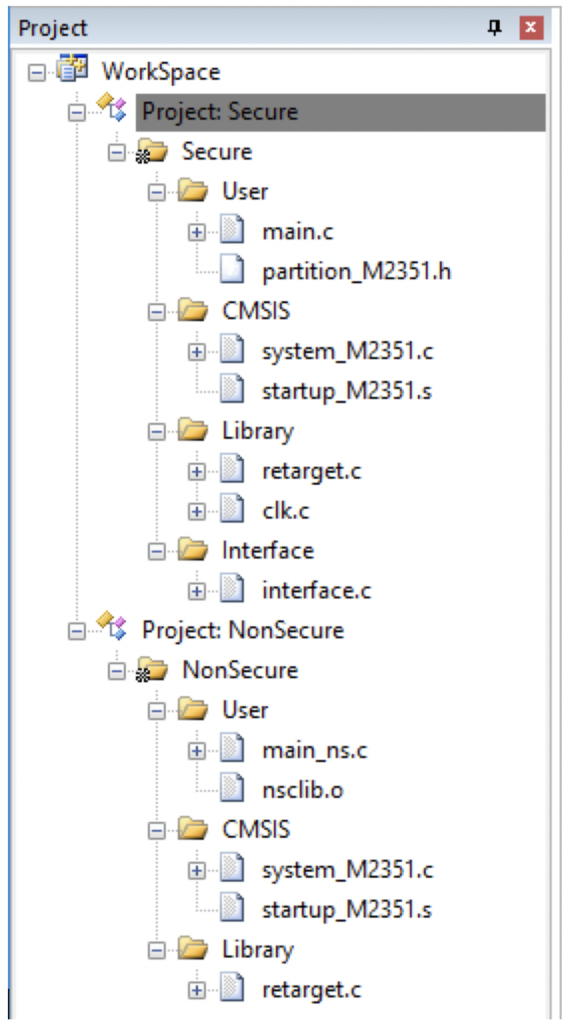
Developers will want to review and modify the partition_<device>.h file which contains the Secure Attribute Unit (SAU). The SAU is used to set which memory regions, interrupts and peripherals are secure and non-secure.
There are several different resources that developers will want to keep an eye on when they are starting to use TrustZone. First, there is the Arm community page for the armv8-m architecture which is located at https://community.arm.com/processors/trustzone-for-armv8-m/. There are several blog postings and white papers that can serve as a great reserve for getting up to speed quickly.
Second, in addition to the Arm website and materials, I also put together a 1-hour introduction webinar on TrustZone back in January 2018 that covers the fundamental concepts and demonstrates a bare-metal and RTOS based application on hardware. That can be found at http://bit.ly/2BI7iPK.
While Arm TrustZone for the Cortex-M is new and just starting to hit the market, it has the potential to become a major tool in helping developers secure their embedded systems. While hardware may not yet be readily available, starting out with simulated examples and understanding the implementation and software model can go a long way in helping developers become ready for when the technology does become common place.
References