Complying with MISRA-C is more complex than running a static analysis tool and calling it good. Compliance is heavily dependent on agreement between stakeholders on what compliance means. Compliance requires the development team to have a solid software development lifecycle (SDLC), including clear requirements. While claiming compliance can be complex, verifying that your software complies with MISRA-C directives and rules can often be done using a static analysis tool.
(Not all directives and rules can use an analyzer and may require other verification methods).
There are many tools available that teams can use to analyze their code base for MISRA-C compliance. For example, there are open-source tools like cppcheck; However, these tools often require a little extra work to sync the output with the rules. One tool I have often used for MISRA-C compliance checking is SciTools Understand.
SciTools Understand Overview
SciTools Understand is a software IDE and tool that helps engineers understand their code base. It can help developers navigate legacy code, visualize software architectures, and generate code metrics. As you can imagine, this is a great tool for consultants when they need to go in and make heads and tails of customer code in the quickest timeframe.
The tool offers some cool features like the generation of dependency graphs like the one shown below in Figure 1:
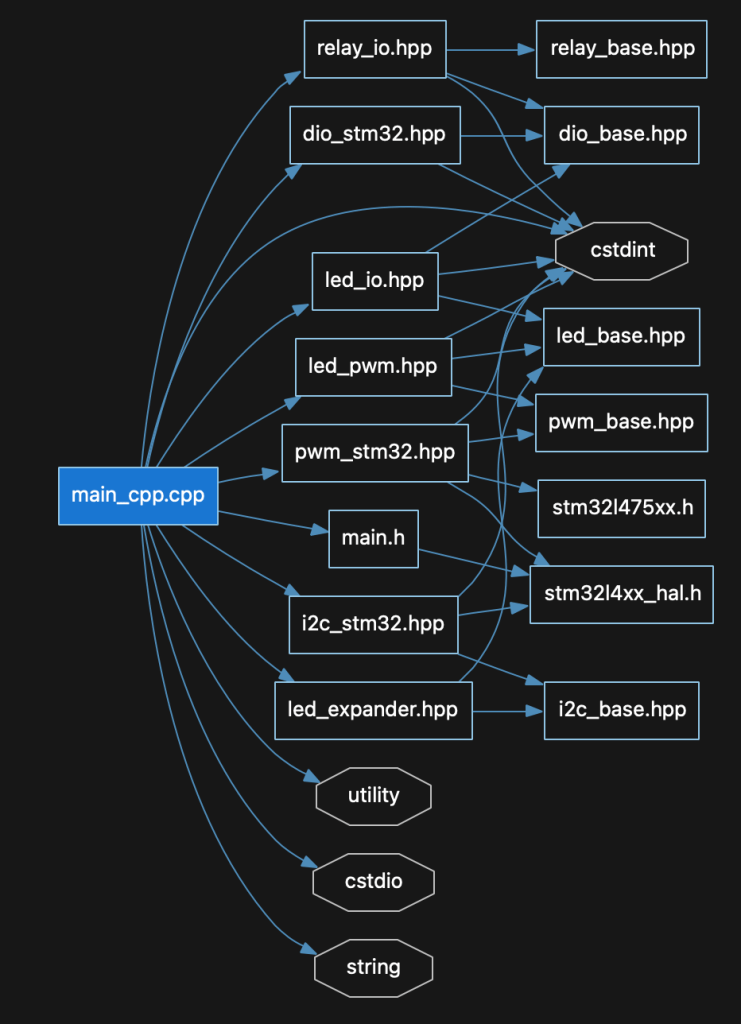
Figure 1 – Example Project Dependency Graph
I’ve also found the treemap feature to be very helpful. For example, Figure 2 below shows the cyclomatic complexity of all the functions in an example project, including vendor-provided code:
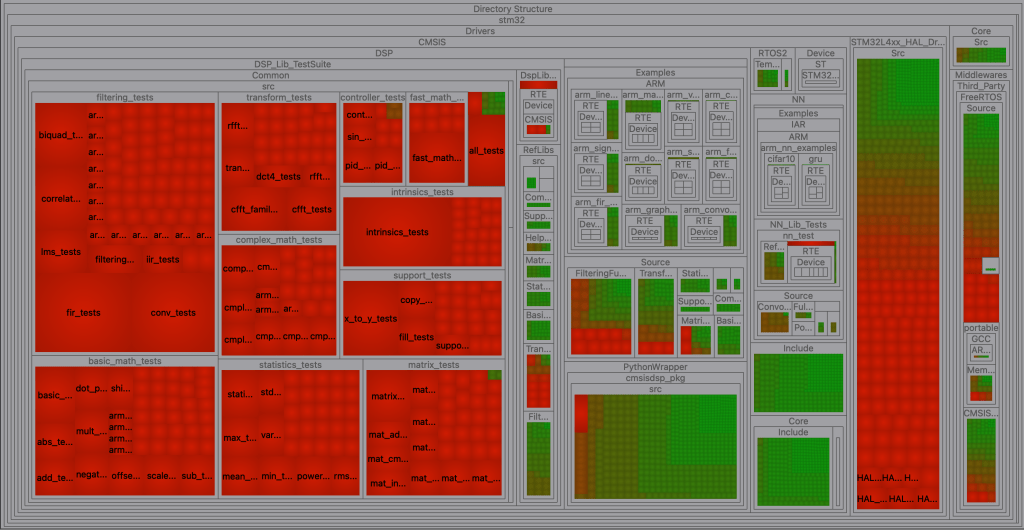
Figure 2 – Example Treemap of Cyclomatic Complexity from SciTools Understand
These are some of the features I originally started using Understand for. However, I quickly discovered that the tool also had a static analysis feature to analyze code for various coding standards, including MISRA-C!
MISRA-C Compliance Checking
Understand includes a tool called CodeCheck that can be configured to verify MISRA-C directives and rules that can be statically analyzed. As you can see in Figure 3, I’ve configured the tool to check for MISRA-C:2012 on some test code. The tool can check against several other standards as well, including AUTOSAR and Effective C++, amongst several others.
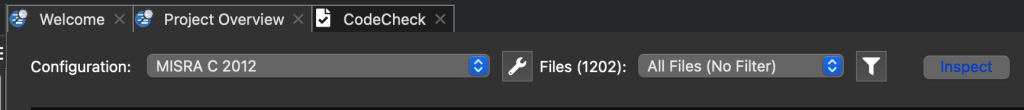
Figure 4 – Understand CodeCheck can be used to analyze software statically for MISRA-C Compliance.
After selecting the standard to check against, a developer must click inspect, and the analyzer will run through the code. There are options to filter which files are checked based on directory structure along with most recently modified. I often recommend that developers initially focus on the code they write, not on vendor libraries they may use. Vendor code is often a rabbit hole, and the stakeholders will define whether they must be included in MISRA-C compliance.
Figure 4 shows an example of the results that you might get analyzing a code base:
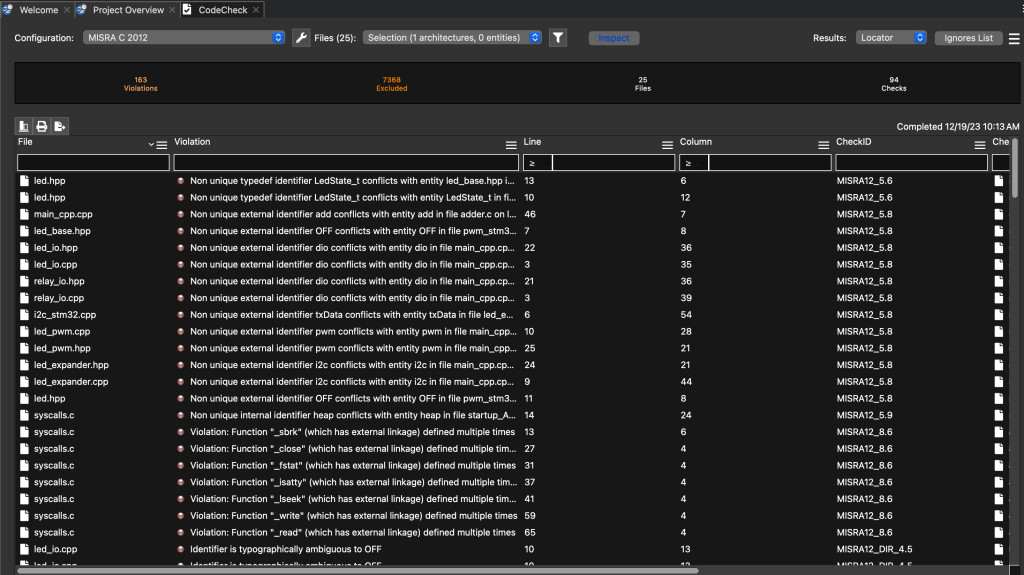
Figure 4 – The results of a CodeCheck analysis for MISRA-C:2012
MISRA-C Static Analysis Results
Once you have the results of CodeCheck, you can click on each violation to investigate it. CodeCheck provides information about the file and line number of the violation, along with which rule was violated. That can be extremely useful in understanding where your code might require modification. Might is the keyword here. You may find a false positive in the violation, like any static analysis tool. You may also find that the tool points out a potential issue, and the specific MISRA-C rule requires manual verification. The tool can help get you close, but a developer has to take the compliance the rest of the way.
If you find a rule violated, you have a few options available. First, verify that the issue is real. Next, you can fix the issue. Finally, if there is a good reason for violating the rule, you can silence the violation using a code comment if you have a deviation record or permit. If you don’t have one, you can follow the process you have in place to try and get one.
Conclusions
MISRA-C compliance can only be claimed for a project. To be MISRA-C compliant, you must negotiate with your customer what MISRA-C compliance means. Even if you don’t want to claim MISRA-C compliance, trying to have your code comply with the standard can help ensure that you develop quality embedded software. After all, you want to minimize defects and issues, which is exactly what following MISRA-C directives and rules will get you. While many tools are available to help you analyze your code, I’ve used SciTools Understand for years. It has helped not just to analyze coding standards but also to keep close tabs on other software metrics and code dependencies that can affect scalability and software quality.





